Note: this was converted from LaTeX to Markdown using ChatGPT 4.1. The original PDF can be found here along with the bibliography.
Secure data storage on Windows
Laboratory protocol
Exercise 8: Secure data storage on Windows
Class: 3AHITN
Name: Stefan Fürst, Justin Tremurici
Group Name/Number: todo/12
Supervisor: SPAC, ZIVK
Exercise dates: 14.02.2025 | 21.02.2025 | 28.02.2025 | 7.02.2025
Submission date: 14.3.2025
Table of Contents
- Task definition
- Summary
- Exercise Execution
- Introduction
- Explaining the first script
- The second script
- Creating Users and Adding Them to Groups
- Resizing the Disk and Creating a New Partition
- Creating Directories
- Populating the Directories
- Creating Users and Groups
- Verifying the Creation of users and groups
- Managing NTFS Permissions Using icacls
- Sharing the Directories via SMB
- Encrypting the Volume using BitLocker
- References
Task definition
Task Overview
The goal of this exercise is to set up a secure and structured data storage system on a Windows Server, ensuring proper access control and encryption. The tasks include installing the operating system, configuring users and groups, setting up a folder structure, and securing access with permissions.
First, Windows Server 2019 or newer must be installed in a virtualized environment, with the hostname and user accounts configured according to a naming convention. A structured folder system should be created based on an assigned fictional company, categorizing data logically and including sample files.
User management involves defining necessary accounts, organizing them into organizational groups, and enforcing a consistent naming scheme. Permissions must be applied using NTFS security settings, restricting access appropriately. Network shares need to be configured to allow remote access while maintaining security through controlled sharing settings.
The storage system must be optimized by creating a new partition, migrating data, and applying BitLocker encryption. All configurations should be verified, and documentation is required throughout the process. PowerShell automation is encouraged where applicable.ChatGPT1
Summary
This task was fully automated using two PowerShell scripts. The first script set up the environment by configuring the necessary system settings and creating a Scheduled Task using New-ScheduledTask and Register-ScheduledTask to execute the second script at predefined intervals. The second script performed all required operations, including creating and managing users, directories, files, and their permissions.
To manage users, the script utilized commands such as New-LocalUser to create users, Add-LocalGroupMember to assign them to groups, and Set-LocalUser to modify user settings. The script dynamically generated random user accounts and assigned them to groups based on predefined logic. Organizational groups and security groups were structured to align with the fictional company scenario, BuildSmart BIM, a digital building company specializing in architecture, material lists, and time plans.
For managing directories and files, commands like New-Item were used to create directory structures, and icacls was used to configure NTFS permissions for securing access.
The partitioning of the drive was accomplished using Resize-Partition to shrink the primary partition and New-Partition to create a new B: partition, followed by Format-Volume to prepare it for use. The existing directory structure was then migrated using Move-Item.
To enable file sharing, New-SmbShare was employed to create network shares. Additionally, the script encrypted the partition using Enable-BitLocker.
Through this approach, the entire process was streamlined and executed automatically, significantly reducing manual effort while maintaining a structured and secure environment.
Exercise Execution
Introduction
This entire exercise was automated with a script that can be invoked with a single command. It is designed to be used after setting up a fresh install of a new version of Windows Server. This script will complete the entire exercise automatically.
Note: For the script to work, the language of the Windows Server installation must be set to English, since user and group names are localized with no available aliases.Nico Boehr2
To run it, simply log into the Administrator account, press Windows + R to open the Run dialog, and paste the following command:
powershell.exe iwr https://tinyurl.com/mr234bdr | iex
This runs powershell.exe and uses the abbreviation iwr, which stands for Invoke-WebRequest. This command makes a web request to the given link, which in this case is https://tinyurl.com/mr234bdr. This URL redirects to the raw file from my GitHub repository, where the first of two PowerShell scripts is downloaded.Invoke-WebRequest3
Important: Whenever you run a command like this, always open the URL in your web browser first to verify its contents. Check whether the script has any red flags, such as obfuscation or suspicious behavior that it is not intended to perform.
The downloaded script is then piped into iex, which is short for Invoke-Expression. This executes the output from stdin, which, in this case, is the contents of the script.Abbreviation Table4Invoke-Expression5
Explaining the first script
Changing the execution policy
The first line of the setup.ps1 script is:
Set-ExecutionPolicy RemoteSigned -Scope LocalMachine -Force
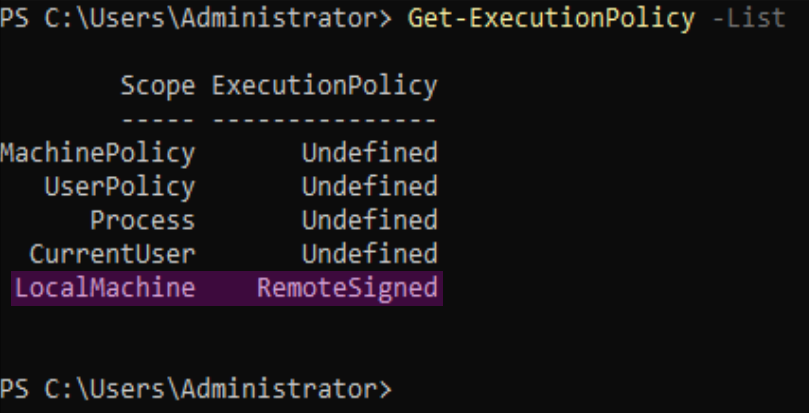
This sets the ExecutionPolicy parameter to the RemoteSigned policy. The Scope parameter specifies the default scope value in this command as LocalMachine. The -Force parameter is used to suppress all confirmation prompts. So that the second script that is downloaded in this script is allowed to run on this device.Set-ExecutionPolicy6
This can be verified by running the following command:
Get-ExecutionPolicy -List
Installing BitLocker
Install-WindowsFeature BitLocker installs the Windows feature BitLocker, which is used for drive encryption and will be needed later in the exercise. It is included in the setup because its installation requires a reboot.Install-WindowsFeature7BitLocker8
Changing the Hostname
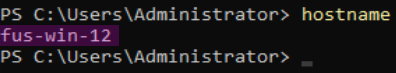
Rename-Computer -NewName "fus-win-12" -Force changes the hostname of the computer to fus-win-12. The -Force parameter ensures the command runs non-interactively. This requires a reboot as well and is therefore included in the setup script.rename-computer9
The change of the hostname can be verified by using the hostname command:
Downloading the second script
To download the second script, Invoke-WebRequest is used again with a url and dest variable to store the desired URL and destination file.
$url = "https://raw.githubusercontent.com/Stefanistkuhl/obsidianschule/refs/heads/main/3.Klasse/itsi/aufgaben/windoof/script.ps1"
$dest = "C:\Users\Administrator\script.ps1"
Invoke-WebRequest -Uri $url -OutFile $dest
Enabling Remote Desktop
For easier management and testing of users, we choose to enable Remote Desktop.
Set-ItemProperty -Path 'HKLM:\System\CurrentControlSet\Control\Terminal Server' -name "fDenyTSConnections" -value 0
Enable-NetFirewallRule -DisplayGroup "Remote Desktop"
Enable-Remote-Desktop10
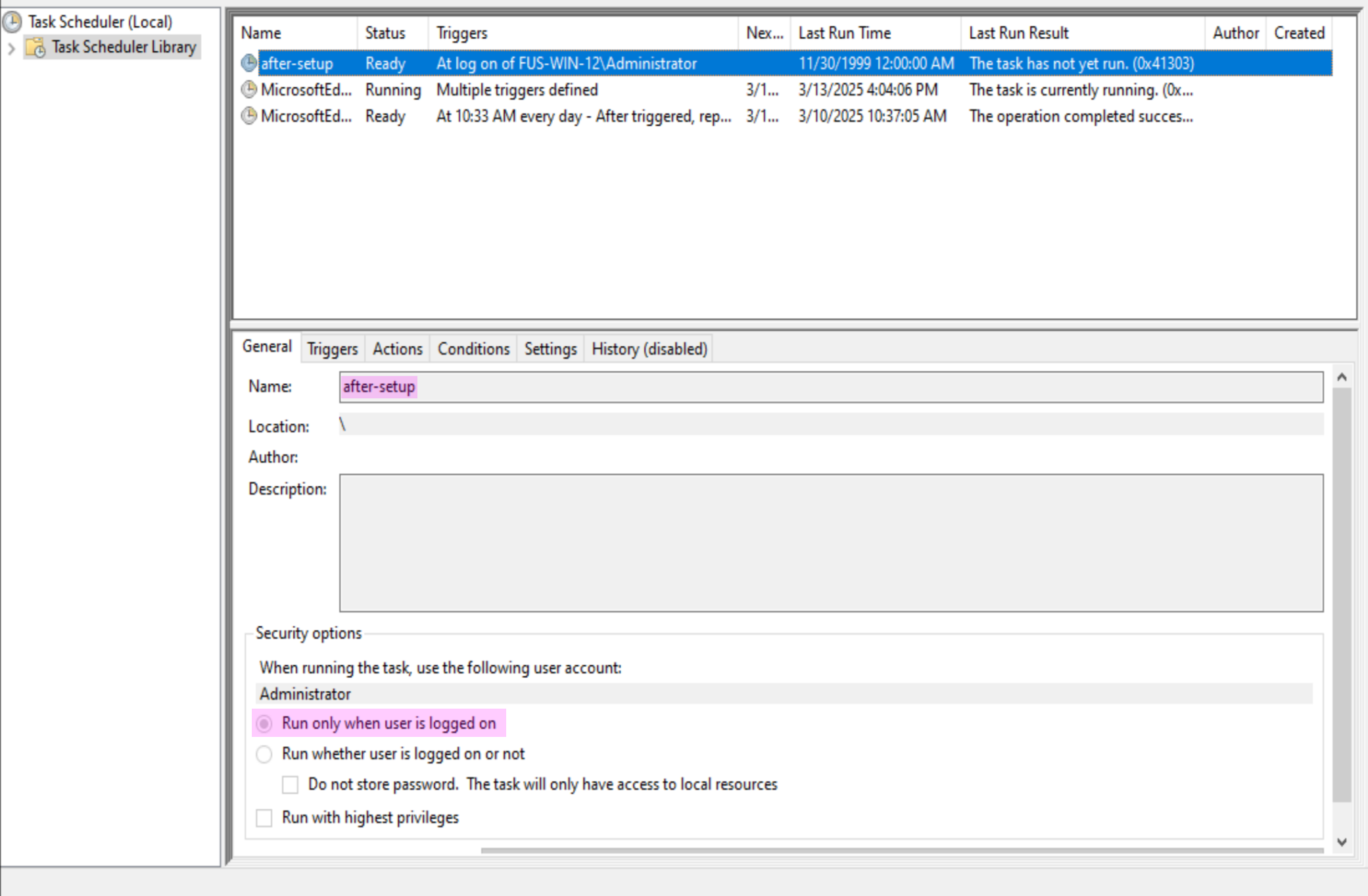
Creating a Scheduled Task
Since a restart is needed for the first part, some form of persistence is required for the second script to execute. For this, Windows Scheduled Tasks are used to execute the second script after a reboot with a set trigger.New-ScheduledTask11
$Action = New-ScheduledTaskAction -Execute "powershell.exe" -Argument "-file C:\Users\Administrator\script.ps1"
$Trigger = New-ScheduledTaskTrigger -AtLogon -User "Administrator"
$Settings = New-ScheduledTaskSettingsSet
Register-ScheduledTask -TaskName "after-setup" -Action $Action -Trigger $Trigger -Settings $Settings
Restart-Computer
The second script
Now that the setup script has finished running, after logging in as the administrator again, the second script will be launched.
Creating Users and Adding Them to Groups
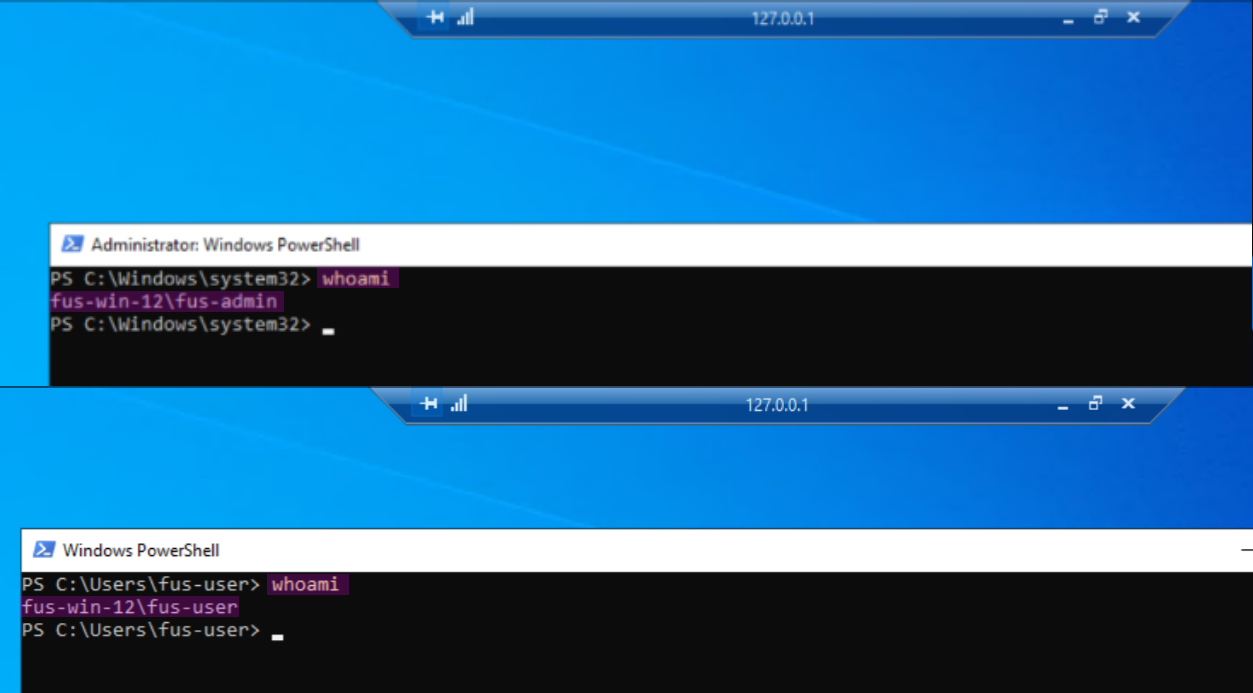
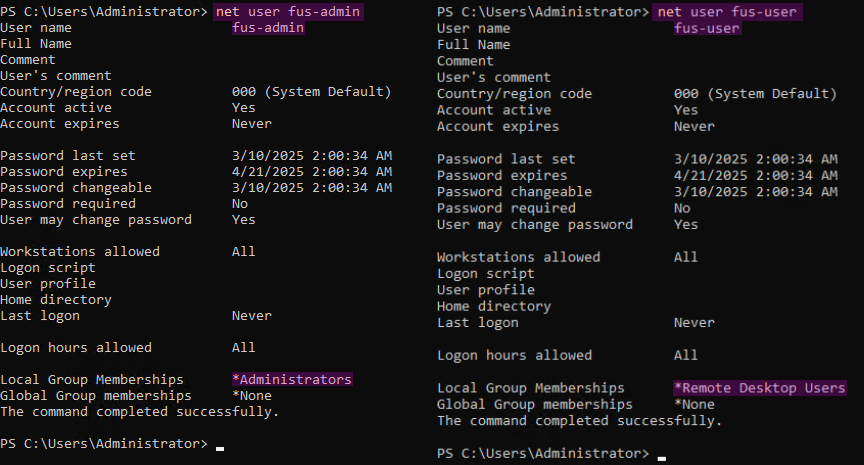
In this step, two new users will be created: fus-admin and fus-user. These serve as the administrator’s low-privileged account and privileged account, respectively, in this scenario.
$supersurepassword = ConvertTo-SecureString "rafi123_" -AsPlainText
New-LocalUser -Name 'fus-admin' -Password $supersurepassword
New-LocalUser -Name 'fus-user' -Password $supersurepassword
Add-LocalGroupMember -Group "Administrators" -Member fus-admin
Add-LocalGroupMember -Group "Remote Desktop Users" -Member fus-user
ConvertTo-SecureString12New-LocalUser13Add-LocalGroupMember14
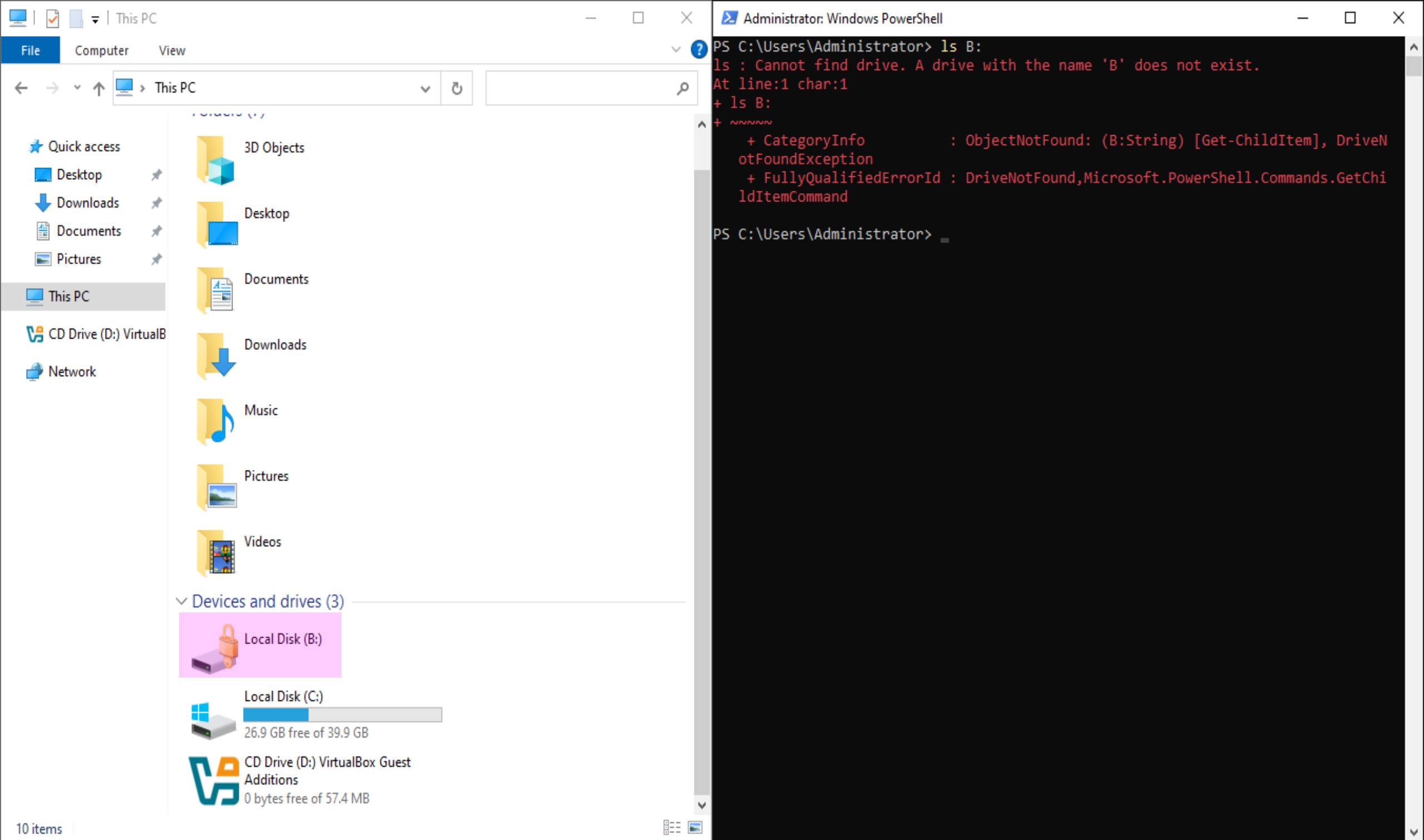
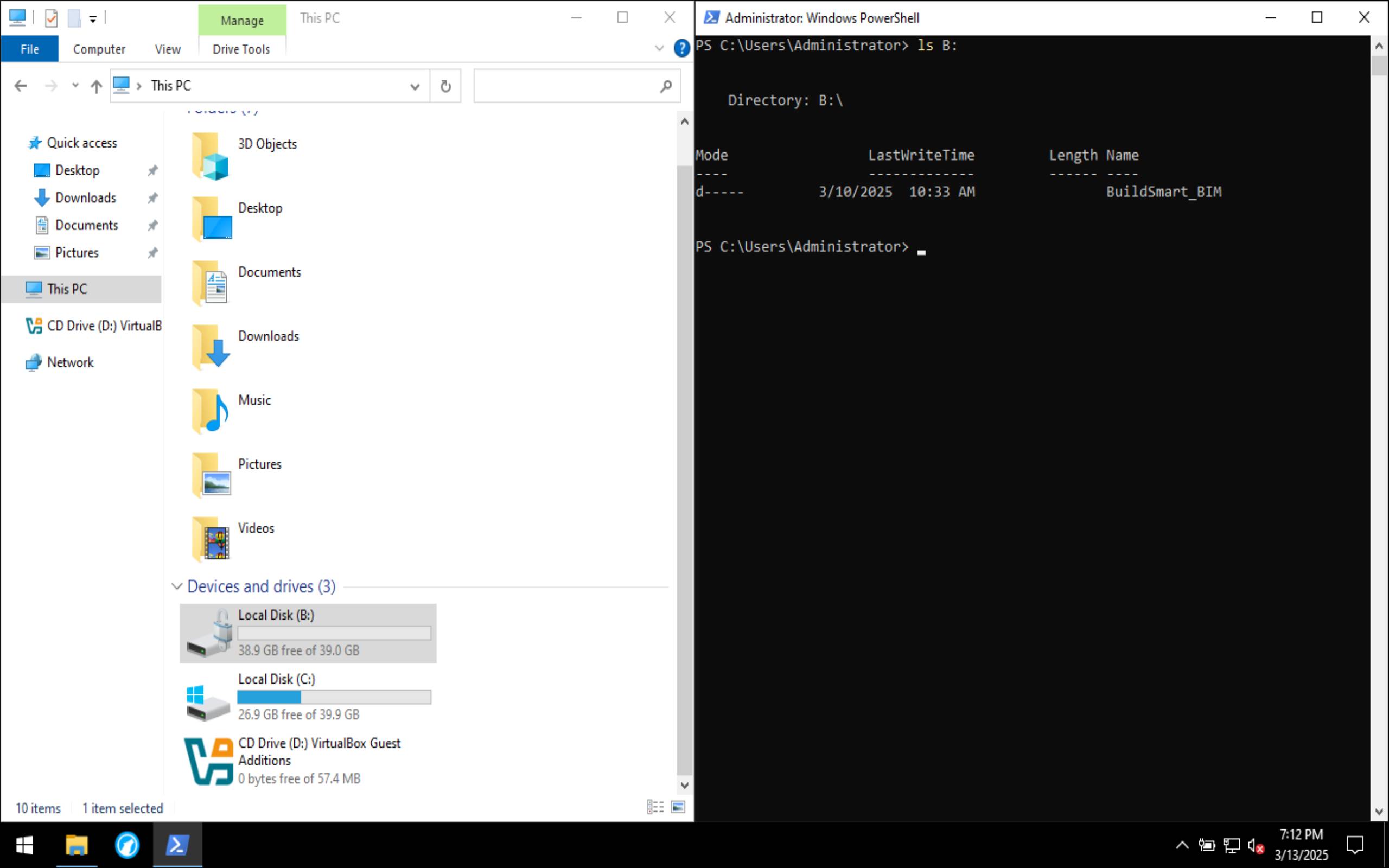
Resizing the Disk and Creating a New Partition
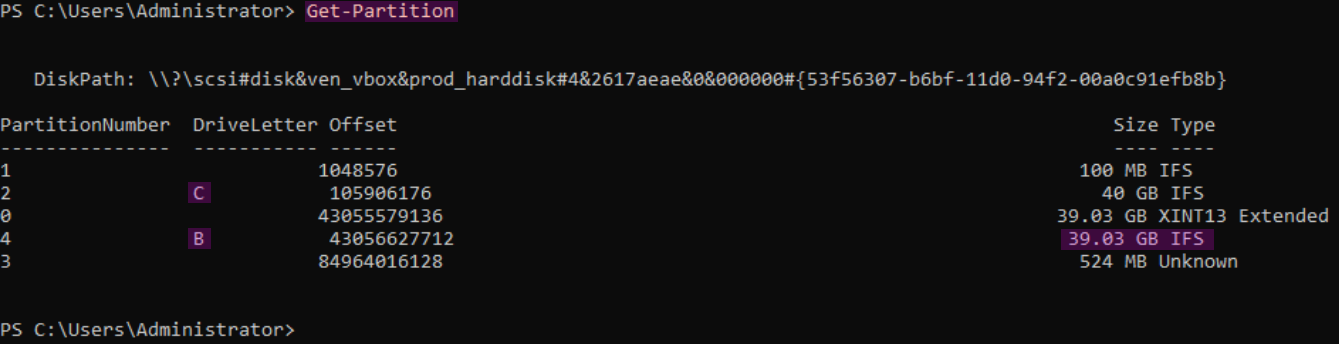
Resize-Partition -DiskNumber 0 -PartitionNumber 2 -Size (40GB)
New-Partition -DiskNumber 0 -UseMaximumSize -DriveLetter B
Format-Volume -DriveLetter B -FileSystem NTFS -AllocationUnitSize 4096
Resize-Partition15New-Partition16Volumes17Cluster-Size18Format-Volume19Cluster-Size-220
Creating Directories
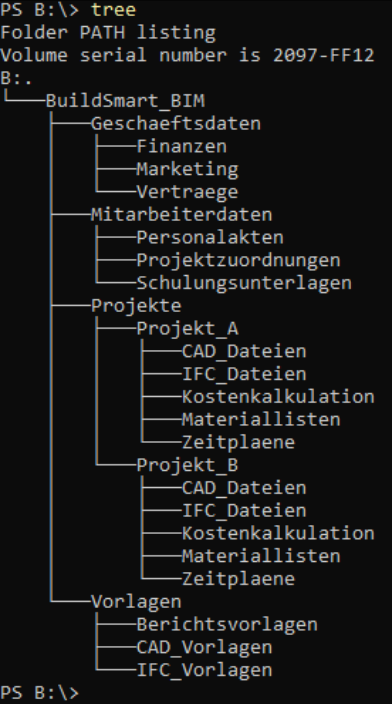
$baseDir = "B:\CompanyData"
$folders = @(
"Administration",
"Finance",
"HumanResources",
"IT",
"Legal",
"Marketing",
"Sales"
)
foreach ($folder in $folders) {
New-Item -Path $baseDir -Name $folder -ItemType Directory
}
Populating the Directories
$sampleFiles = @(
"Budget.xlsx",
"EmployeeList.csv",
"ProjectPlan.pptx",
"Report.docx"
)
foreach ($file in $sampleFiles) {
foreach ($folder in $folders) {
New-Item -Path "$baseDir\$folder" -Name $file -ItemType File
}
}
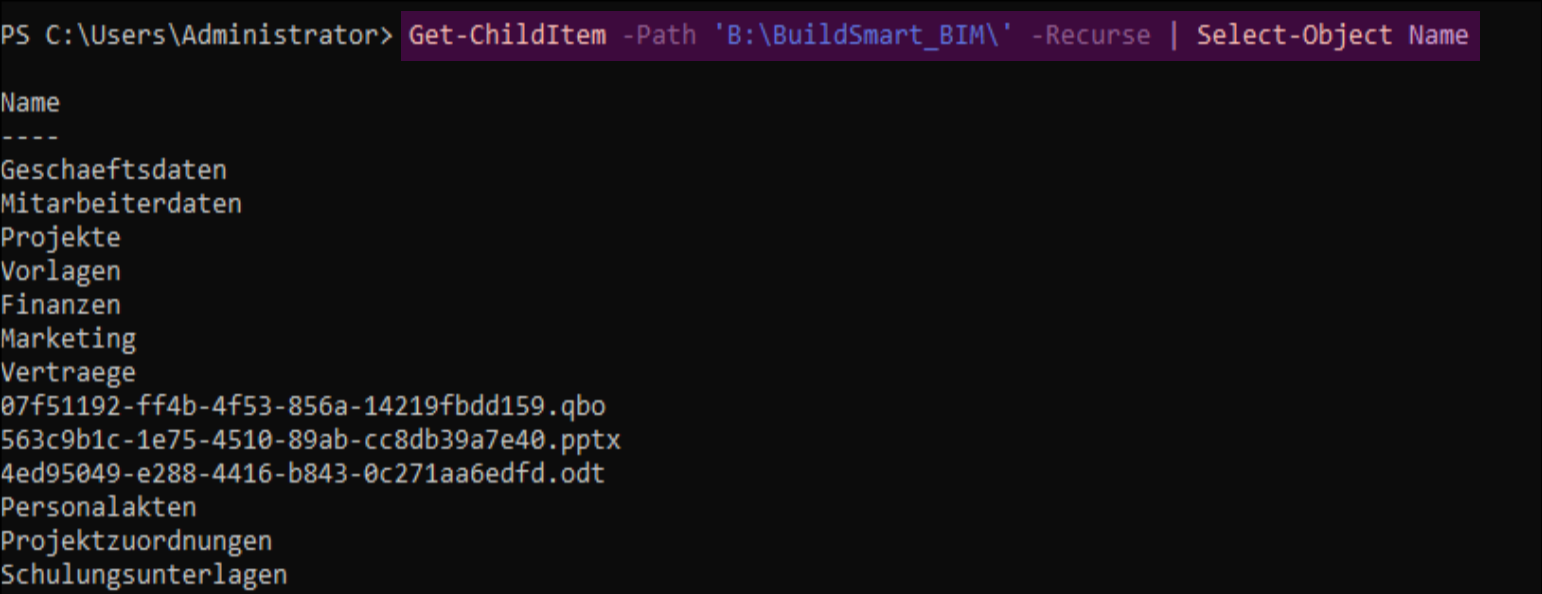
Creating Users and Groups
$groups = @("Admins", "Users", "Guests")
$users = @("alice", "bob", "charlie")
foreach ($group in $groups) {
New-LocalGroup -Name $group
}
foreach ($user in $users) {
$password = ConvertTo-SecureString "P@ssw0rd" -AsPlainText
New-LocalUser -Name $user -Password $password
Add-LocalGroupMember -Group "Users" -Member $user
}
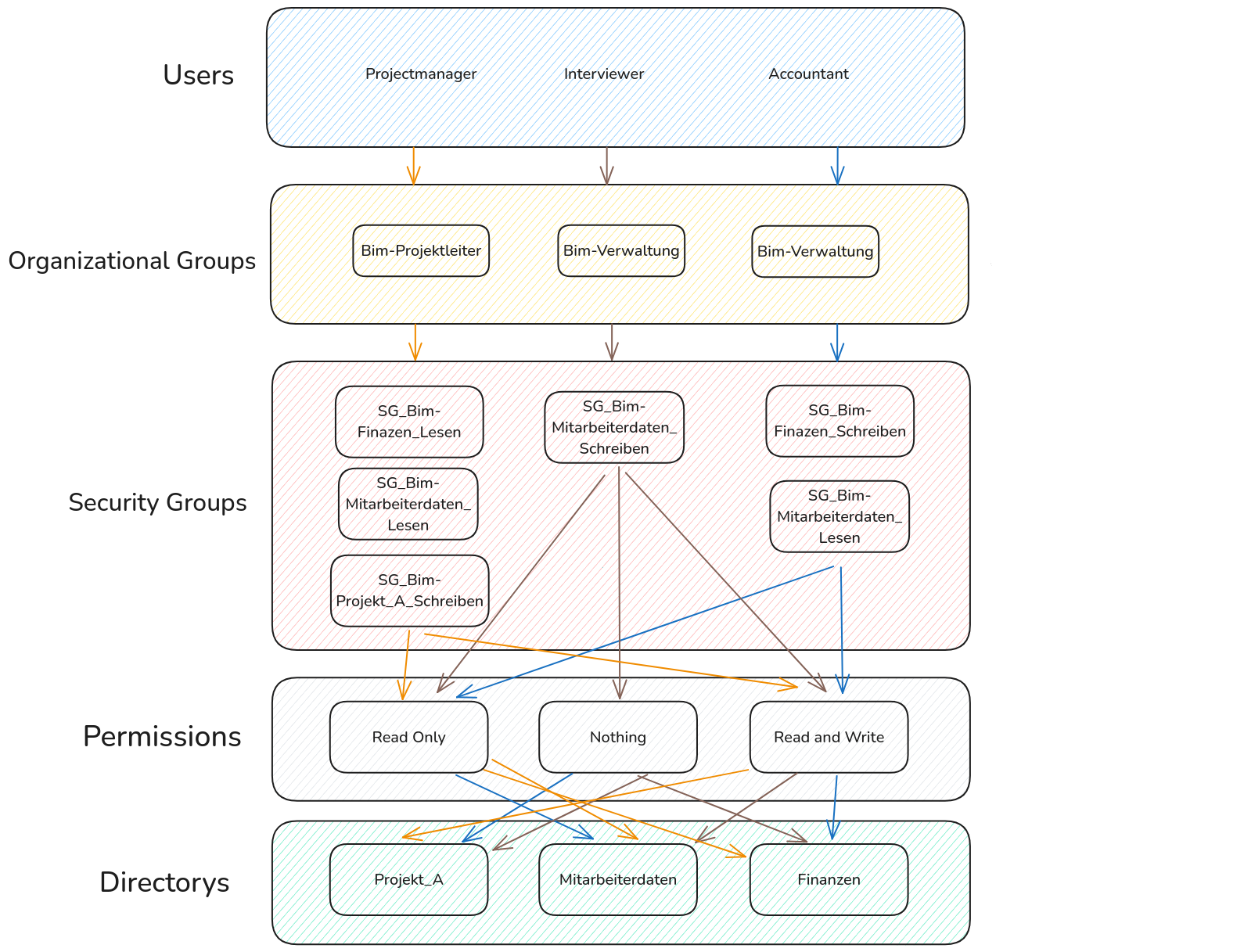
Verifying the Creation of users and groups
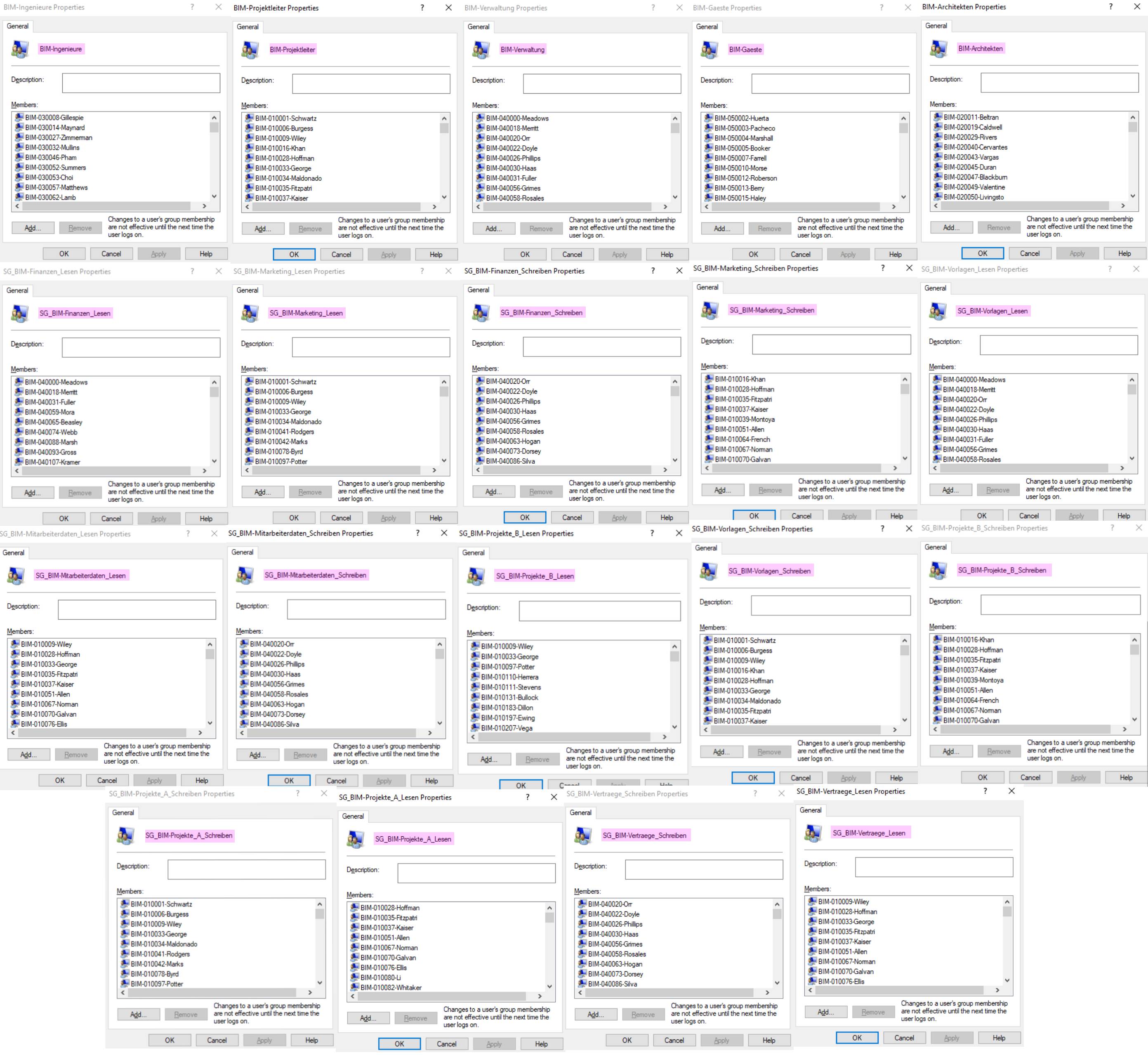
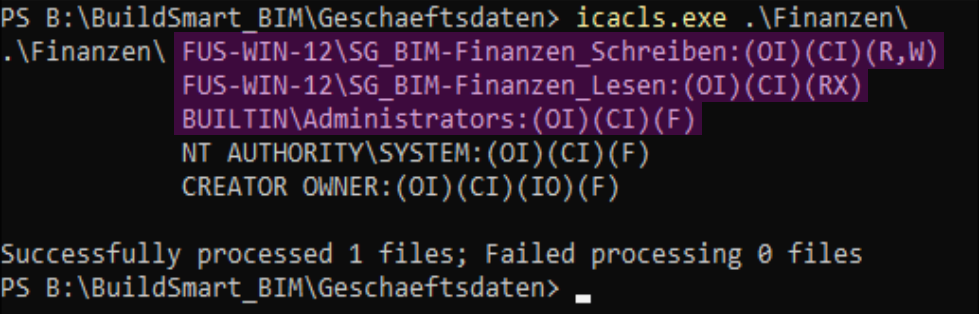
Managing NTFS Permissions Using icacls
icacls "B:\CompanyData" /grant:r "Administrators:(OI)(CI)F" /T
icacls "B:\CompanyData" /grant:r "Users:(OI)(CI)RX" /T
icacls "B:\CompanyData" /grant:r "Guests:(OI)(CI)R" /T
Sharing the Directories via SMB
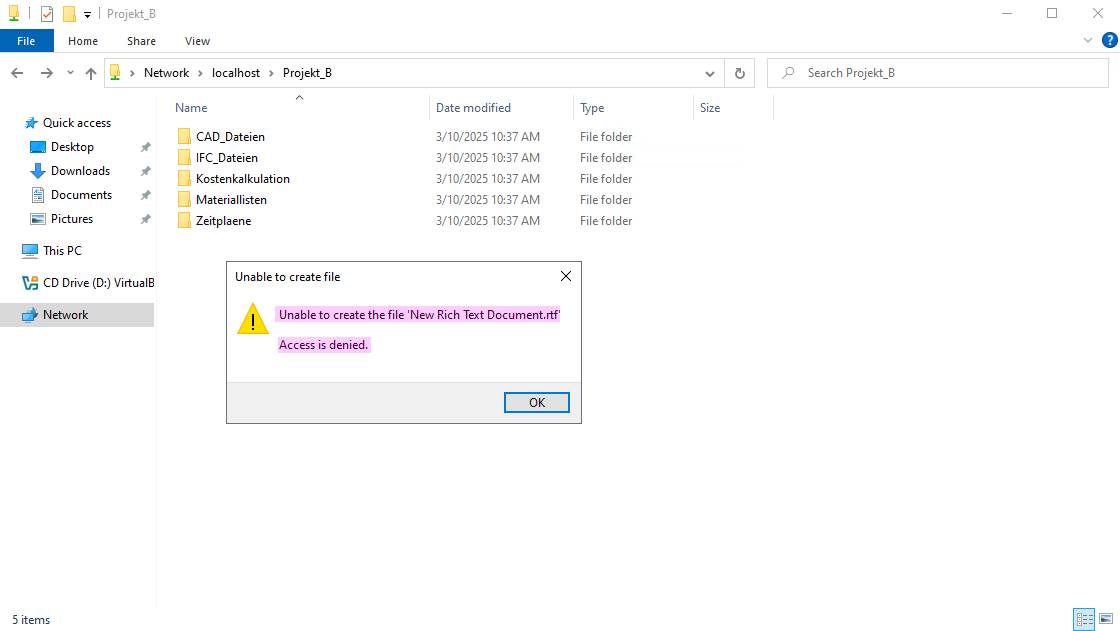
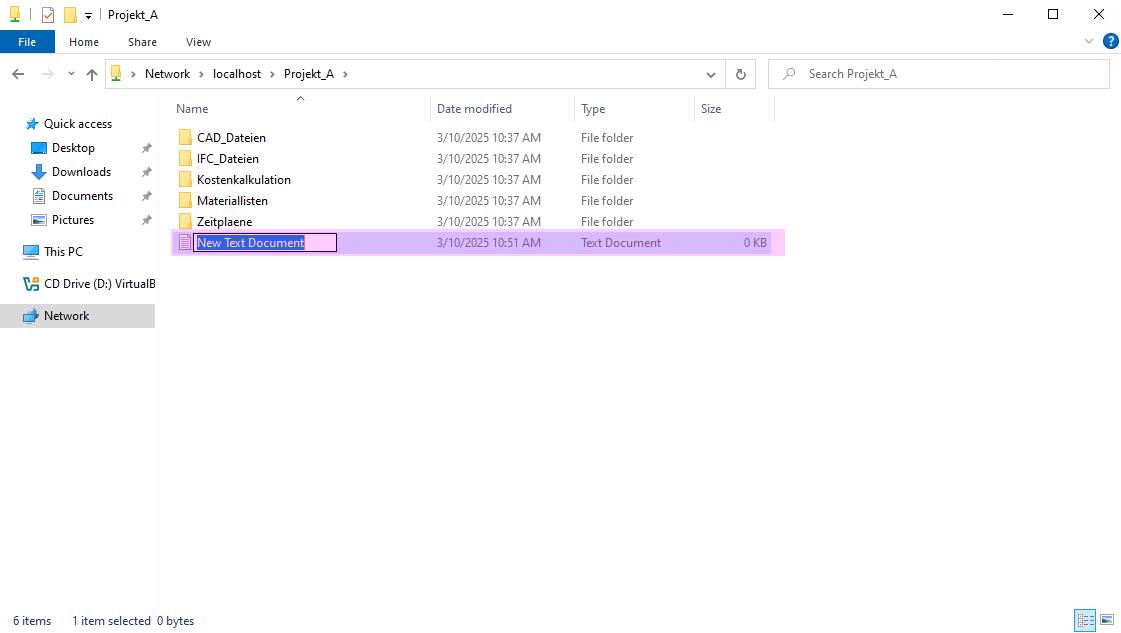
New-SmbShare -Name "CompanyData" -Path "B:\CompanyData" -FullAccess "Administrators","Users" -ReadAccess "Guests"
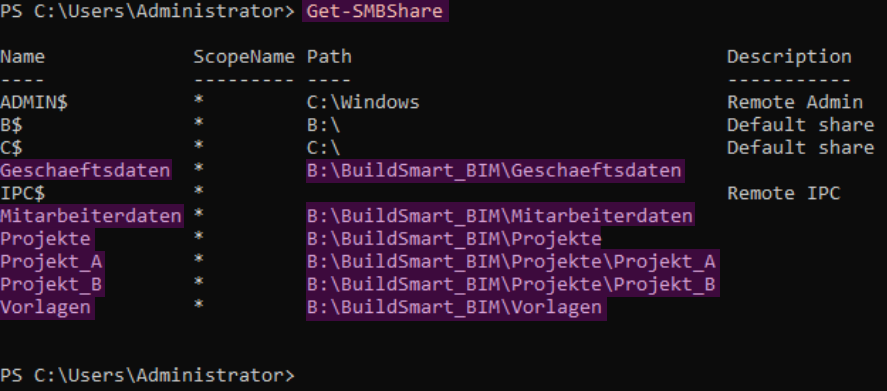
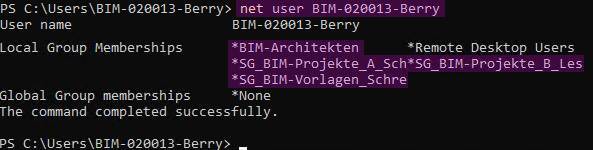
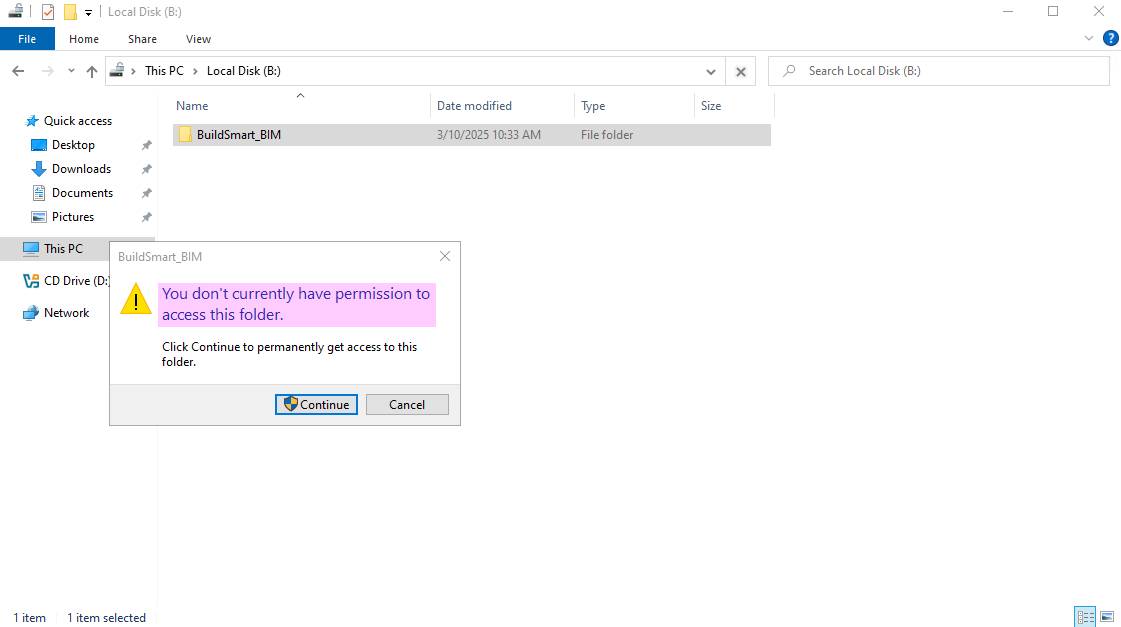
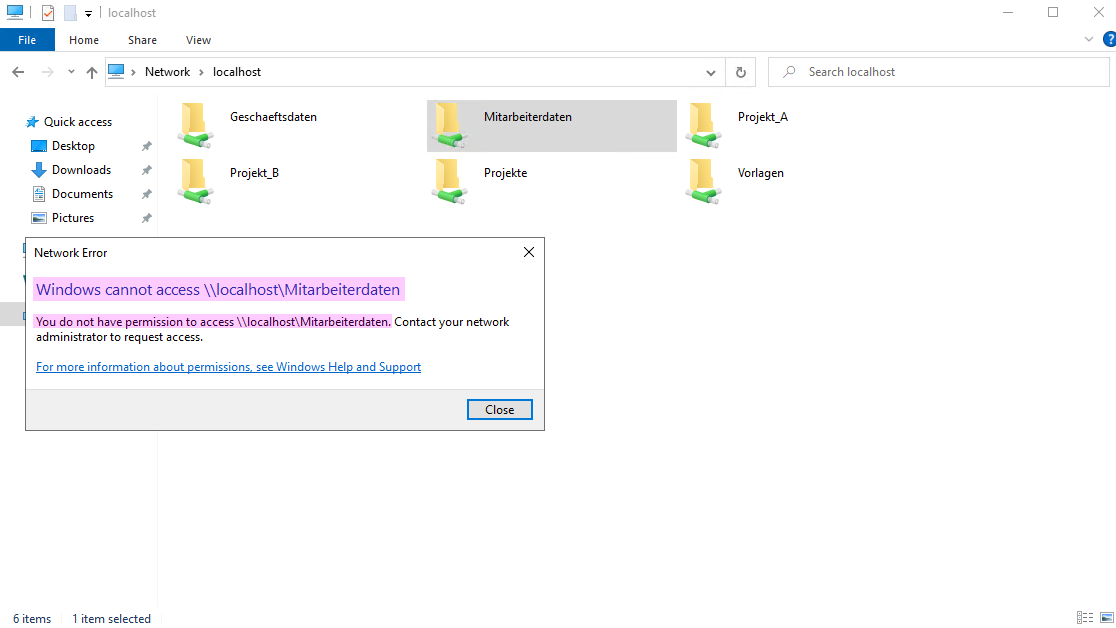
Now, users can only access the files they need via the network share. Since in Section 3.2.10, permissions to the root directory were removed, users do not have access to the entire file structure. In this scenario, this is a central server where each employee either has a local workstation or a thin client and connects to the server remotely.
Encrypting the Volume using BitLocker
Enable-BitLocker -MountPoint "B:" -EncryptionMethod Aes128 -PasswordProtector -Password $supersurepassword
Enable-BitLocker21
References
For a full bibliography, see the original BibTeX file.
This task definition was generated using ChatGPT. ↩︎
Nico Boehr. Localized Names of Users and Groups in Windows. source ↩︎
sdwheeler. Invoke-WebRequest (Microsoft.PowerShell.Utility) - PowerShell. source ↩︎
Agoston, Zsolt. PowerShell Abbreviation Table | OpenTechTips. source ↩︎
sdwheeler. Invoke-Expression (Microsoft.PowerShell.Utility) - PowerShell. source ↩︎
sdwheeler. Set-ExecutionPolicy (Microsoft.PowerShell.Security) - PowerShell. source ↩︎
JasonGerend. Install-WindowsFeature (ServerManager). source ↩︎
sdwheeler. Rename-Computer (Microsoft.PowerShell.Management) - PowerShell. source ↩︎
PowerShell FAQs. How to Enable Remote Desktop Using PowerShell? source ↩︎
sdwheeler. ConvertTo-SecureString (Microsoft.PowerShell.Security) - PowerShell. source ↩︎
sdwheeler. New-LocalUser (Microsoft.PowerShell.LocalAccounts) - PowerShell. source ↩︎
sdwheeler. Add-LocalGroupMember (Microsoft.PowerShell.LocalAccounts) - PowerShell. source ↩︎
Laxmansingh@twc. What is difference between Partition, Volume and Logical Drive. source ↩︎
Watumull, Garrett. Cluster size recommendations for ReFS and NTFS. source ↩︎
Amanda. What Is Allocation Unit Size & How to Change It - MiniTool Partition Wizard. source ↩︎